On-boarding and Deploying Your First Devices on the Helium Network - Part 1
LoRaWAN Sensor and Device Unique IDs and Security Credentials
All LoRaWAN sensors and devices have the ability to connect to any LoRaWAN network. Onboarding is the process of connecting the unique ID and credentials of an unprovisioned LoRaWAN device to the owner's specific account on their selected network. The LoRaWAN protocol defines two secure and encrypted methods that LoRaWAN devices follow to join a network: Over-The-Air Activation (OTAA) and Activation By Personalization (ABP). OTAA is recommended for most LoRaWAN device deployments and is the method that we will cover in this section. All LoRaWAN devices support at least one of these join methods; the vast majority of commercially available LoRaWAN devices support OTAA by default.
LoRaWAN devices come pre-programmed with the following unique IDs and security credentials which support the OTAA onboarding method:
|
Name |
Description |
Size |
|
DevEUI |
A global end-device ID in the IEEE EUI64 address space that uniquely identifies the end device across all LoRaWAN networks. |
8 bytes |
|
AppEUI or JoinEUI* |
A global application ID in the IEEE EUI64 address space that uniquely identifies the join server that is able to process the Join procedure and derive the session keys. |
8 bytes |
|
AppKey |
An AES-128 root key specific to the end device, used whenever it joins a network. The AppKey is used to derive the session keys (NwkSKey and AppSKey) specific to that end device to encrypt and verify network communication and application data. |
16 bytes |
Note
The AppEUI has been renamed. In the latest LoRaWAN specification it is referred to as the JoinEUI to better describe its critical function.
When purchasing a LoRaWAN sensor, you will typically find the EUIs printed on a label or QR code that is either inside or outside of the device.
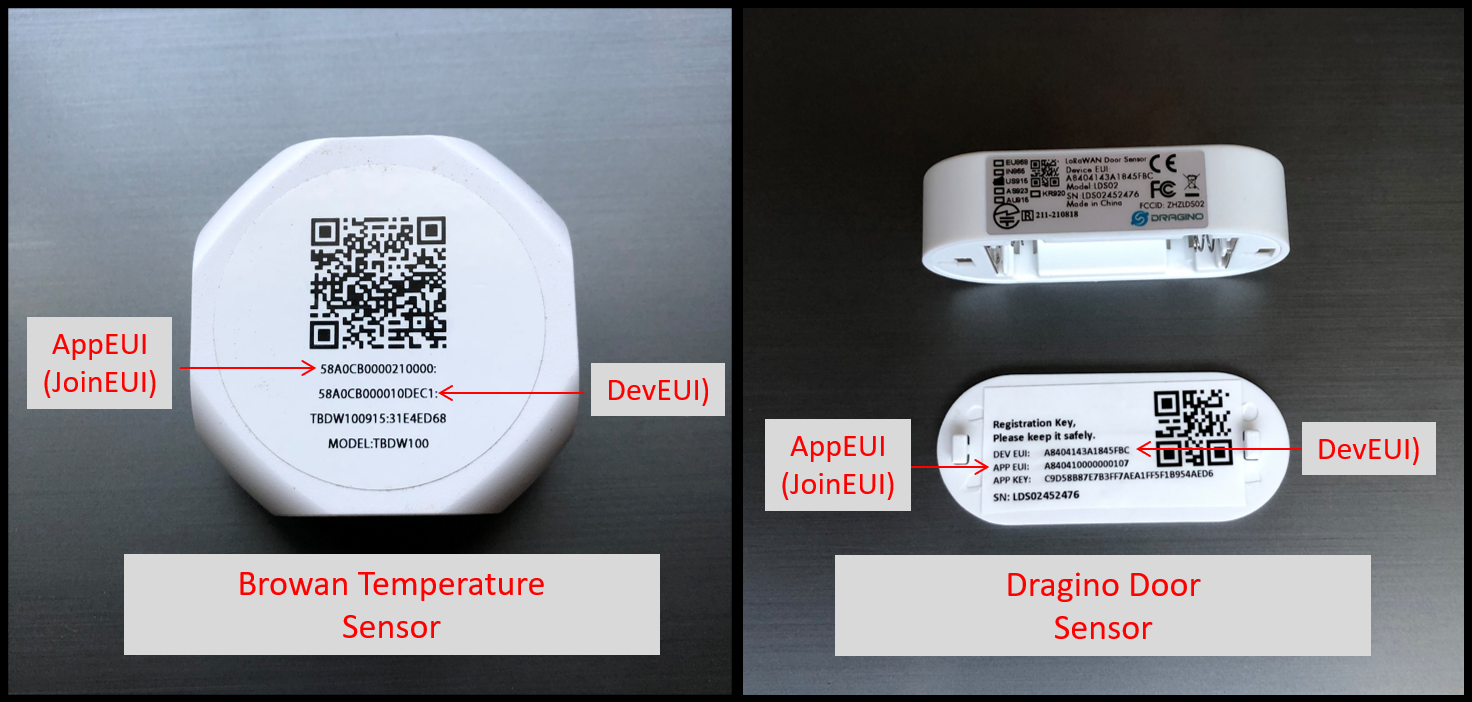
Examples of Browan and Dragino LoRaWAN Sensors with printed EUIs.
In addition to the DevEUI and JoinEUI (AppEUI), it’s essential that the AES-128 AppKey is also provided to onboard a device. The LoRaWAN network security is predicated on the NIST-approved and standardized AES cryptographic algorithms, which require the secrecy of the AppKey to be maintained. The LoRa Alliance provides extensive documentation on LoRaWAN security that provides full details of best practices for end-to-end security.
When you purchase a LoRaWAN device, there are a number of places you might find the corresponding AppKey:
- Printed on the label (common for low-volume purchases)
- Sent securely to the purchaser in a flat file (CSV) or via API integration
- Available via a device claim service, which allows the purchaser to access the keys via a website and securely download or connect them via API
For high-volume commercial deployments, the customer may dictate to the device manufacturers the exact details of desired EUIs, AppKeys, and back-end integrations. A customer-specific JoinEUI (AppEUI) may be needed for deployment scenarios that require devices to roam on non-Helium LoRaWAN networks, including those using the Helium packet purchasing method. In this case, the customer would need to either configure each device’s JoinEUI (AppEUI) or have the manufacturer inject the customer-specific JoinEUI (AppEUI) at the time of manufacturing.
The level of security required is specific to each LoRaWAN IoT deployment. There are a number of commercial options to increase the security measures protecting the secrecy of the AppKey, from silicon manufacture to network onboarding, including the use of Semtech’s LR1110/1120 devices with the LoRa Cloud join server and Device Claim functionality.
For many IoT deployments, the default EUIs and AppKeys meet the solution requirements, and they will be used for our example project.
In the example above, the Dragino door sensor included the AppKey on the device’s printed label under the battery cover. Take care to remove this label or obscure the AppKey on the label after onboarding.
In other cases, the AppKey will not be printed on the device, but will be provided by the reseller or the manufacturer in a CSV file or a claim utility. For example, the Browan temp sensor does not print the AppKey on the label; its AppKey is provided via a secure link to a CSV file after purchase by the reseller.
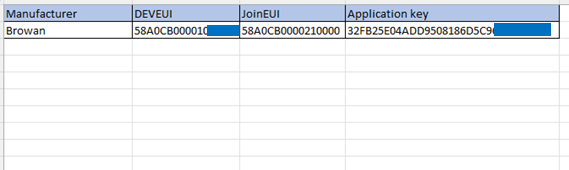
AppKey provided in downloaded CSV file