1 - End Device Activation
This book covers LoRaWAN® end-device activation in depth.
Todo
Add more details
Over-the-Air Activation (OTAA) Device Provisioning
Step 1: Provision End Device with Keys
The following keys must be provisioned (stored) on the end device in non-volatile memory (NVM) when the device is manufactured: Device Extended-Unique-Identifier (DevEUI), Join Extended-Unique-Identifier (JoinEUI), and Application Key (AppKey).
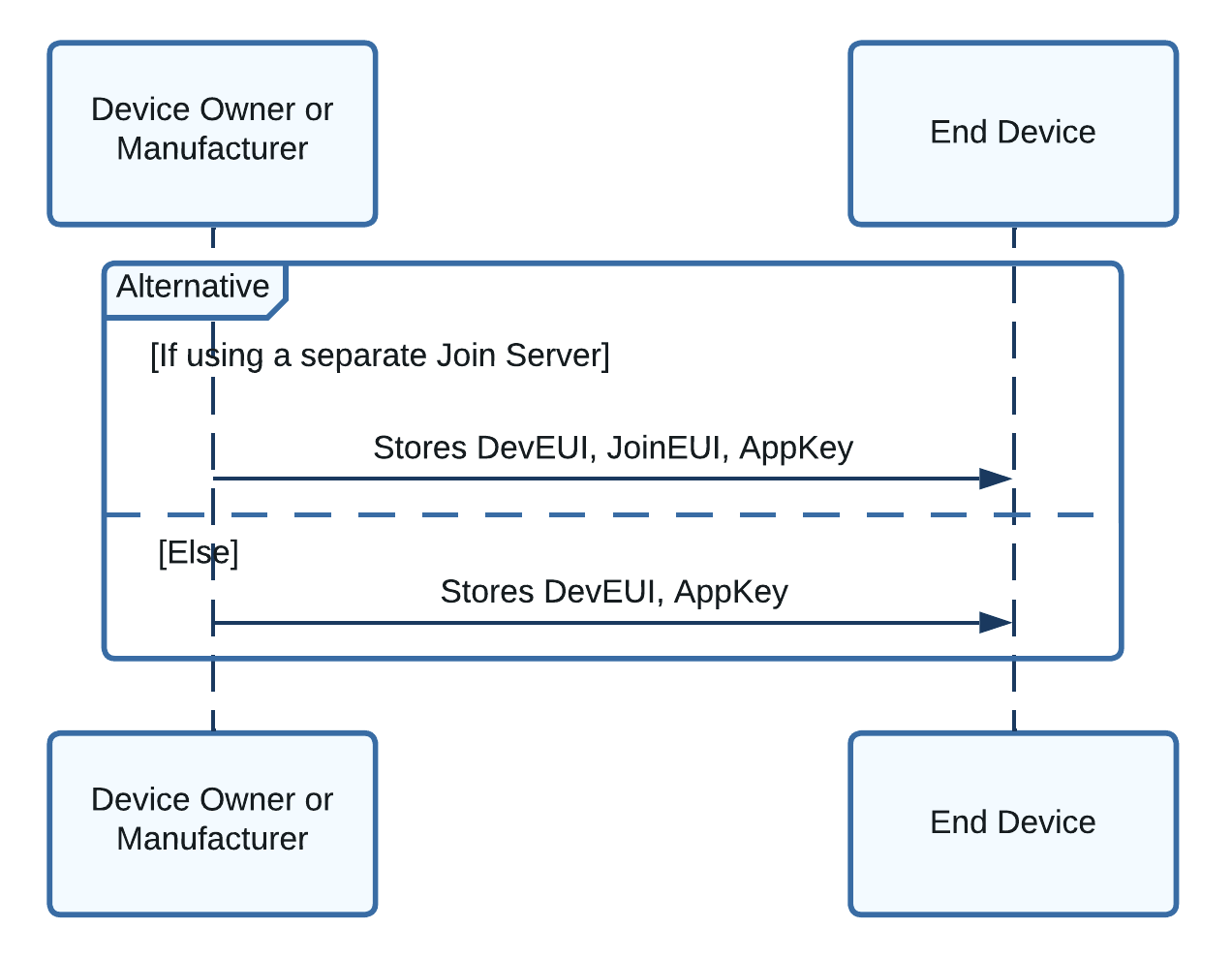
Figure 1: Sequence diagram showing the keys provisioned on the end device
You are responsible for obtaining these keys, as described in this section.
Note
A good practice is to print the DevEUI on the cover of the end device to ease device management. Document TR005 LoRaWAN® Device Identification QR Codes explains how to generate a QR code containing the DevEUI and JoinEUI. Never include the AppKey in this QR code, and never show it on the cover of the end device.
Device EUI (DevEUI)
The DevEUI is a globally unique 64-bit identifier in the Institute of Electrical and Electronics Engineers (IEEE) EUI-64 address space that uniquely identifies the end device.
The manufacturer of the radio module may have already provisioned the module with a valid DevEUI. If not, or if you cannot use the provisioned DevEUI, you must obtain your own globally unique DevEUI. Learn about obtaining a DevEUI for commercial use by reading Section 2.2, ‘Extended-Unique Identifier’ (page 7) and Section 2.5.1, ‘Device EUI’ (page 8) of TR007 Developing LoRaWAN® Devices V1.0.0. Further advice on obtaining a DevEUI is found in Developing LoRaWAN-based Devices: Things to Know, DevEUI.
Warning
It is essential that you obtain unique addresses for your devices when you put them into production. Do not invent your own DevEUIs. Once one of your devices has been shipped to a customer, it can be joined to any network; if another device on the network already uses the same DevEUI as your device, your customer won’t be able to add your device to their network.
In addition, use of a globally unique identifier enables your device to use LoRaWAN® roaming. If supported by the network server your end device is registered with, roaming enables the use of gateways provided by other network servers which participate in a roaming scheme with your own network provider. Learn more about roaming in Section 11, Roaming Procedure (page 22) of LoRaWAN® Backend Interfaces Technical Specification (TS002-1.1.0).
Join Server Identifier (JoinEUI)
The Join Server Identifier (JoinEUI) is a unique identifier used to support the use of a join server that is separate from the network server. By utilizing a separate join server, an additional layer of security is added that prevents the network server from accessing the AppSKey. As a result, the network server is unable to decrypt any application-specific messages sent to and from the device, enhancing the confidentiality of the data. Learn more about the separation of network server and join server in TS2-1.1.0 LoRaWAN Backend Interfaces Specification.
The JoinEUI is an identifier in the Institute of Electrical and Electronics Engineers (IEEE) EUI-64 address space that identifies which join server to use to handle the join process. This join server must be provisioned with the devices AppKey and DevEUI before the join process begins.
The JoinEUI is supplied to you by the operator of the join server you are using. Many devices will use the same JoinEUI.
If you are not using a join server separately from the network server, choose one of the EUIs that you own to be the JoinEUI to use across all your devices. Using a valid EUI as the JoinEUI will enable you to use an external Join Server in the future.
Warning
Do not invent your own JoinEUI. Do not generate a unique JoinEUI for each device.
Note
In LoRaWAN Link Layer Specifications prior to 1.0.4, JoinEUI is referred to as AppEUI.
Application Key (AppKey)
The application key (AppKey) is an Advanced Encryption Standard (AES) 128-bit root key unique to the end device. The AppKey is used by both the end device and the join server to derive the NwkSKey and AppSKey session keys during the OTAA process, and to verify the integrity of the Join Request and Join Accept messages sent during the OTAA process as part of the MIC.
Read Section 2.5.3, ‘Root Keys’ (page 9) of TR007 Developing LoRaWAN® Devices V1.0.0 to learn how to securely generate and store root keys such as the AppKey.